Partnering Leading Security and Networking Companies to Gain Full Visibility into SSL Traffic
To ensure effectiveness against cyber-attacks using SSL, A10 Networks offers SSL Insight, an essential feature in the A10 Thunder ADC which eliminates the SSL blind spot in corporate defenses and enables security devices to inspect encrypted traffic – not just clear text.
The Thunder ADC intercepts SSL traffic, decrypts it temporarily to make it visible and forwards it to third-party security devices for inspection. Once the traffic has been analyzed and scrubbed, Thunder ADC encrypts it once again to be processed as normal SSL traffic, forwarding it to the intended destination. In the diagram below, Thunder ADC is placed at the client side and external router side, having security devices installed in between for inspection of SSL traffic to detect sophisticated cyber attacks. Decryption and re-encryption of SSL traffic can also be done with a single device, by using Thunder ADC’s virtualization feature called the "Application Delivery Partition (ADP)" that enables a single physical device to be partitioned logically to act as multiple devices.
Protection Against Targeted Attacks Using SSL Insight
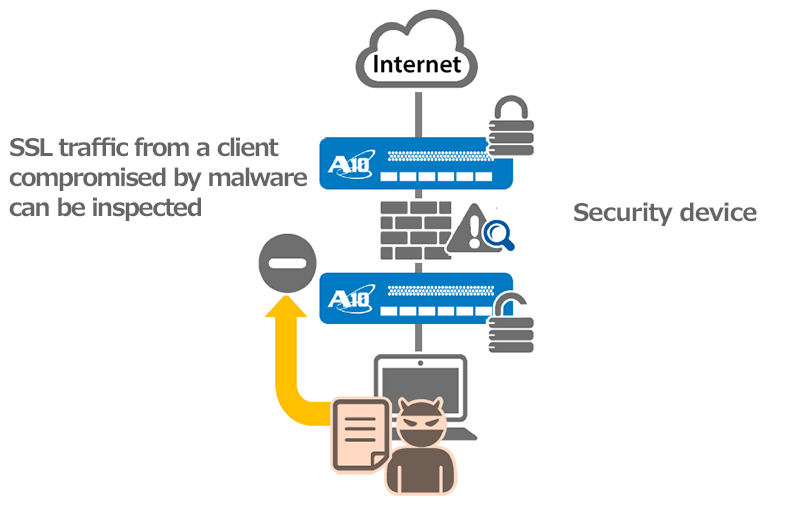
Key points:
- Conventional security devices cannot inspect encrypted traffic (SSL traffic), or performance may deteriorate
- With A10 Thunder ADC SSL Insight feature, traffic can be inspected while maintaining high performance
Benefits:
- High-speed processing with dedicated hardware
- Integration with various security devices (i.e. third party UTM, URL filter, proxy, etc.)
- Information leakage can be prevented
- Virtualization feature that allows single device deployment
Source: A10 Networks
Kumamura explains the benefits of using SSL Insight as follows:
"With conventional security devices, performance of critical business applications may deteriorate as they are rarely designed to encrypt SSL traffic at high speeds. In some cases, some security products cannot decrypt SSL traffic at all. With A10 SSL Insight, SSL traffic can be inspected at a very fast rate."
According to some analysts, the proportion of attacks in which encrypted traffic is used to circumvent defensive systems is forecast to reach as much as 50% by 2017. However, the survey also revealed that currently almost no measures have been taken to deal with this. The ratio of organizations who do not decrypt and inspect encrypted communications using security devices such as firewalls, intrusion prevention system (IPS), and unified threat management (UTM) is more than 80%.
With regard to security devices and SSL processing load, it is said that performance deteriorates significantly in situations where SSL certificate with a 2048-bit key is used, with average deterioration in performance of around 81%.
SSL Insight provides effective countermeasures against targeted attacks and the variety of cyber-attacks that uses SSL. Kumamura says main benefits are "high-speed SSL processing with dedicated hardware, and flexibility to be used with a variety of third party products, such as sandboxes, URL filters, proxies, next generation firewalls, and UTMs. "
For example, integration with next generation firewalls which are known for their "sandbox" functions. Next generation firewalls actually run new types of malware and other malicious software that attempt to avoid detection using a signature, observe its behavior, and determine whether it is a threat or not. This boasts a high detection rate, but some of those firewalls do not support SSL communication, and cannot handle encrypted attacks. If those are used with SSL Insight, high detection rate which those already have, can be increased to the absolute maximum.
