SSL connections are being increasingly used in order to provide a secure environment for Web usage. However, also on the increase is a new type of cyber-attack in which encrypted communication is exploited to disguise attacks and avoid detection by security products.
SSL is used for confidential communication to ensure critical information such as IDs, passwords, and personal details are not leaked. But in recent targeted attacks, critical information were stolen by methods such as intrusion into an internal network using SSL and communicating with an external command and control (C&C) server.
This page introduces A10 Networks' SSL InsightTM, a feature which eliminates blind spots in SSL traffic by decrypting SSL-encrypted traffic and forwarding it to security devices for inspection.
Featured Contents

[White Paper] Essential Five Requirements: The Ultimate Guide to SSL Inspection for Uncovering Threats in SSL Traffic
Encrypted traffic accounts for a growing percentage of network traffic. To stop cyber-attacks, organizations must gain insight into encrypted data, and to do this, they need a dedicated security platform that can decrypt SSL traffic. This paper describes five features that organizations should consider when evaluating SSL inspection platforms, enabling IT security teams to rapidly develop evaluation criteria and avoid common deployment pitfalls.

[Solution Brief] SSL Insight: Uncover Hidden Threats in Encrypted Traffic
To prevent attacks, intrusions and malware, enterprises need to inspect incoming and outgoing traffic for threats. Unfortunately, attackers are increasingly turning to encryption to evade detection. Read this solution brief to learn about the SSL insight solution enabled by A10 ThunderTM ADC.
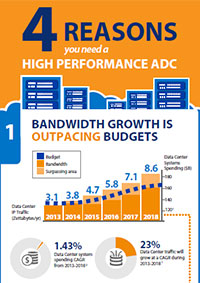
[Infographic] Four Reasons You Need An ADC: What Are the Key Issues for Administrators?
Why is a high performance application delivery controller (ADC) is required? This infographic gives visual hints with four keywords to solve security and performance issues that make IT administrators concerned, such as the squeezing of the IT budget due to vast increases in bandwidth used and increased server loads due to increasing strength of SSL encryption.

[Video] Security Reimagined: State of Evolving Advanced Cyber-attacks
Frequent cyber-attacks such as zero-day attacks that use advanced malware, APT, etc. are causing serious damages. But incumbent security solutions are unable to prevent these attacks effectively. Watch this video presented by FireEye to learn about the current state of evolving cyber-attacks and effective measures to protect your network environments.

